As the coronavirus pandemic continues to spread, cybersecurity experts warn the general public about the rise in cybersecurity threats.
Coronavirus has taken its hold on the western world, with thousands of new cases diagnosed per day globally.
The long-term effects of the virus itself are difficult to assess, much less the long-term effects of the virus on the fabric of society. We do, however, know that as a whole, businesses and individuals are becoming much more focused on utilizing the Internet and technology.
While many jobs and educational opportunities have been remote for a long time, the coronavirus has propelled us into a new era in which it is demanded of us. And with this long-term change comes a new issue: cybersecurity threats.
In this article, we’ll discuss some of the cybersecurity threats we’ve seen pop up in the past couple of months as the virus spreads. We’ll also talk about threats that experts warn could occur, and how you can protect yourself and your business.
Remember; cybersecurity threats are everywhere, and it is best to be proactive rather than reactive.
Let’s take a look at some of the breaches in privacy we’ve seen thus far.
“Zoombombing”
Since the coronavirus pandemic has taken hold of the western world, so has the reliance on Zoom. Zoom is a videoconferencing app that many people are using to keep in touch with one another. It’s being used for everything from substitute classrooms to board meetings to help keep in touch with family members. Churches and temples have even used it to broadcast services so members can feel part of their community.
There are even cabinet and parliamentary debates occurring on the app so that citizens can hear what’s happening.
Unfortunately, hackers have found a way to get into Zoom meetings so that they can broadcast sickening and disturbing images.
Neo-Nazi images were flashed during Holocaust Memorial Day services and ceremonies. Disturbing traumatic images have were sent to Zoom support groups for those recovering from abuse.
This is the latest in one of the many ways people have been breaching cybersecurity measures. “Zoombombing” doesn’t seem to have a purpose beyond serious trolling, as in the perpetrators don’t seem to be gathering users’ private information.
“Zoombombing,” Not Necessarily “Dangerous” But Still Worrying
Still, “Zoombombers” often disseminate photos and text that is illegal in some or all countries. In some cases, the material can be traumatizing, and is often targeted toward specific groups of people.
It is suggested that if your business is using Zoom, that they should ensure their meeting IDs are as private as possible.
While there are companies who cannot make their meetings fully private or do not wish to do so, it is something your company needs to be aware of. As such, making alternate arrangements for meetings or only sharing the URL or ID of the meeting to those invited is one of the best ways to keep a handle on this.
If your business works with young people and is meeting with them via Zoom, it is important that you’re particularly sensitive to this. “Zoombombers” seem to target vulnerable populations, so young people are particularly at risk.
While you should always keep your Zoom IDs private, you should be even more prudent when you work with kids.
Phishing, Taken to New Levels
If you are familiar with cybersecurity or have spent a lot of time online, you’ve likely heard of phishing. But if not, we’ll give you a brief rundown.
Phishing is when a hacker attempts to get your information by having you enter passwords via a third-party app that looks native.
For example, you may get an email from a “company” that closely mirrors PayPal. They may even use PayPal’s logo and have an email address that looks similar to something PayPal would have. For most people, the email will look authentic.
The email may ask that you enter your PayPal information on another page, or click a link where you’ll re-enter your PayPal info. This may be under the guise of needing to “upgrade security” or “confirming your password.” Or, they may say something like they need to upgrade their servers and need everyone’s information.
Unsuspecting individuals will then reply, with their PayPal information, effectively handing it over to hackers. When the hackers have the information, they’re free to use it to get into your PayPal and other financial institutions connected to it.
Other Types of Phishing Attacks
Emails aren’t the only phishing attacks you’ll see online. They can occur on almost any website where a login is required. Talented hackers can mirror websites so that when a login pops up, it looks very similar to the one from a trusted site.
Again, once the person enters their information into the site, they’re effectively handing it over to the hackers.
If a hacker gets ahold of information like bank account details, logins for educational institutions or emails, they can do a significant amount of damage. They can then use this to hack into banking institutions to obtain funds illegally. Or, they can disrupt the business practices of a learning institution or another establishment just to cause chaos.
According to experts, the number of phishing attacks they’ve seen since the Coronavirus pandemic has been exponentially more than usual. While it existed before the epidemic, it seems to have reached pandemic levels in and of itself.
Keeping Yourself Safe from Phishing Attacks
First and foremost, you need to be sure that your systems are secure. Admittedly, this can be difficult when your employees are working remotely and not all logged in to the same server.
However, arming your employees and students and volunteers with antivirus software is an excellent first step. It can help them recognize phishing attacks from the get-go.
Additionally, you and your employees must be educated when it comes to what phishing attacks look like. They should be aware of what to look for and how to authenticate information.
Many companies often send out communications that let their customers know that they will never ask for certain information online. As a business, this is good practice and is worth communicating to your staff and customers.
Let them know that you will never send an email asking for things like bank details, to re-enter their password or any other phishing scheme you may have been a victim of in the past.
Installing Malware
Luckily, there is a group of real-life superheroes looking out for the general public: the COVID-19 CTI (Cyber Threat Intelligence) League. Comprised of over 400 volunteers from a variety of cybersecurity backgrounds, they’ve come together to help protect vulnerable people against such attacks.
One attack they’ve said is on the rise, thanks to COVID-19, is malware. Like phishing, this isn’t new, and it’s been around for quite some time. In fact, most people are probably already familiar with the idea of accidentally installing malware.
Malware is essentially a virus that gets into your computer and finds your personal details or forces your computer to go to a particular site. Often, people are tricked into downloading it, again, thinking they’re receiving an email from a company or financial institution.
Thinking that the email is authentic, people will click whatever they think the institution is asking them for. Then, with the click of their mouse, they’re inundated with malware that makes their computer slow and difficult to use.
For many, taking malware off of a computer can be a huge process, and may even require a professional. This can be a huge headache for businesses, especially since many repair shops are not open or available at present. And if they are, they may require extra time to mail in the computer or equipment.
Both antivirus software and education are important in order to help your staff stay alert for malware.
Again, emailing your customers and letting them know that you won’t ask them to download suspicious links can also be helpful during this time.
Identity “Copying”
Have you ever received a Facebook or Instagram request from someone you swore you were already friends with? You may see that they have another profile, but are adding you again anyway. They may even send you a message that says they have a new profile and want you included in their circle.
This may send off some alarm bells, but most people don’t think twice in re-adding a friend. After all, people lose their passwords or want to become more private all of the time.
But what happens when the person’s messages don’t sound like your family member or friend? Why does their English sound broken or are their speech patterns different?
This is another common scam that is often done to the elderly, as they may not find it as suspicious as younger people. Without a lifetime in technology, they may not see a second profile as bizarre.
Often times, the individual that is “copying” an identity will then friend all of that person’s visible friends to make it seem more authentic. But what do they want?
Most of the time, they are after one of two things: sexual images or cash.
The scam may conclude with an individual asking you to get on Skype or Zoom nude so they can draw you for a class. Or, they may suddenly claim they’re in stuck in another country due to COVID and their cards have been canceled. As such, they “need” you to wire them cash so they can get home. Or, they may give you a link to download, which contains malware.
While this is more often something individuals experience, as opposed to businesses, it is still something to be aware of. Many companies operate with Facebook as well, and some even use private profiles to connect with people.
This scam is one that can only really be deterred through education. But, antivirus software is also important. It can help protect against viruses downloaded through these attacks.
Fake Coronavirus Maps
Yes, hackers have gone that far and have played upon our fears and vulnerabilities: by creating faux coronavirus maps. And while legitimate universities and institutions have authentic maps up for the public, hackers are copying and reposting them.
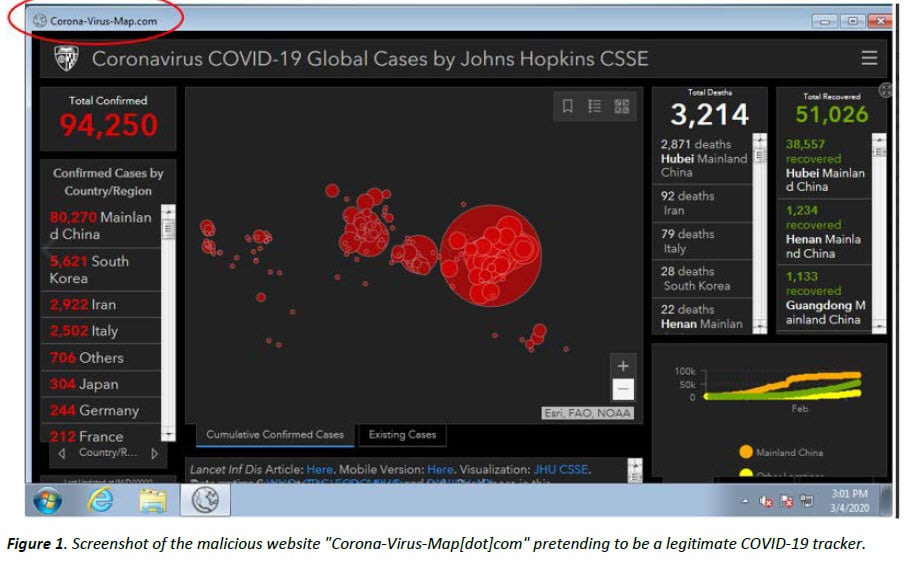
But, how does looking at a fake map harm you? Well, hackers have invented a way! These knock-off maps not only spread false information but also have malware hidden in them once you click on them, bam! The hacker has infiltrated your computer.
As we discussed earlier, malware is a virus that can gather personal information or make it nearly impossible to use your computer. And if your employees are taking company computers home with them, this is a huge problem you’ll need to educate them on.
While anti-virus software is essential, so is ensuring that you and your employees can identify fake maps immediately. Real maps are, no surprise, hosted on real websites like WHO (World Health Organization) and universities.
Fake maps often have servers and URLs that aren’t connected to the real thing in any way.
Keeping Yourself, and Your Employees, Safe from Cybersecurity Threats
Unfortunately, cybersecurity threats never go away. Instead, they adapt to the times. Here at Impact, we can keep your company safe, even while everyone works remotely. We can also offer a managed IT service, so that you don’t have to worry about paying hefty bills for on-site IT people each month.
Ready to keep yourself, and your employees as safe as possible? If so, contact us today, or read our testimonials, to see what we have to offer.


